Not only are healthcare organizations at risk due to cybercrime, so are their patients. Imagine having to turn away patients because your computers are shut down due to a ransomware attack. Or, having to “blindly” treat your patients because you can’t access their medical records unless you pay criminals a ransom. A ransomware attack can halt your workflow, data processing and jeopardize your ability to properly treat your patients.
Patient data is now a popular target for cybercriminals. It can easily be monetized, making healthcare organizations and practices increasingly vulnerable. Believe it or not, ransomware poses even larger risks to patients than failure to properly disinfect medical devices. According to the ECRI Institute:
“This is the first year ransomware has been included in the ECRI Institute’s Top 10 Health Technology Hazards list,” says Juuso Leinonen, senior project engineer at the health devices group. “Cybersecurity topics have been covered in the past, but this is the first year a cybersecurity topic has been ranked No. 1 on the list.”
A New Ransomware Threat–”Defray”
Cybersecurity experts discovered a new ransomware threat that targets healthcare organizations. Defray uses Microsoft Word attachments in emails to infect a network. In one instance it attacked a hospital in the U.K. using an attachment entitled “Patient Report.”
The email looked legitimate because it included the hospital’s logo and the name of the director of information management. Once the attachment was opened, the victim’s files were encrypted.
Defray includes a note asking for $5,000 in bitcoins to return the encrypted files. It also suggests a victim contact them via three email addresses if they have any questions, doubts or want to negotiate. The email addresses contained domains from Russia, Germany, and Switzerland.
There are no tools available to restore files encrypted by Defray. The only thing you can do is restore your files from a recent backup. Unfortunately, some healthcare providers aren’t doing all they can to prevent ransomware attacks, or even backup their data properly in the event their patient information is held ransom.
Medical Devices Are Also Under Attack.
According to a May 2017 article in Forbes, medical devices were hit by ransomware for the first time In U.S. hospitals:
“When the NSA cyber weapon-powered WannaCry ransomware spread across the world this past weekend, it infected as many as 200,000 Windows systems, including those at 48 hospital trusts in the U.K. and so-far unnamed medical facilities in the U.S. too. It wasn’t just administrative PCs that were hacked, though. Medical devices themselves were affected too.”
The Food and Drug Administration is especially concerned about the safety of medical devices. Suzanne Schwartz, M.D., associate director for science and strategic partnerships at the FDA’s Center for Devices and Radiological Health, writes:
“A computer virus or hack resulting in the loss of or unauthorized use of data is one thing. A breach that potentially impacts the safety and effectiveness of a medical device can threaten the health and safety of an individual or patients using the device.”
Manufacturers, hospitals, and other facilities must work to prevent these pervasive cybersecurity threats. With the development of innovative technologies, protecting patients’ safety from malware attacks must be a priority. However, this is difficult when hospitals and healthcare centers use many different types of medical devices from a multitude of vendors.
The Solution? – A Defense-in-Depth Strategy
Mitigating the risk of data breaches and malware infections requires professional IT service and support from experts who are up to date on the latest cybersecurity threats and who utilize defense-in-depth strategies.
Originally coined in a military context, the term refers to an even more comprehensive security strategy approach than layered security. If one layer of protection is breached, the attack can be defended with one or more of the other layers. Layered security is only one part of a defense-in-depth strategy.
Defense in depth addresses a broad range of tactics to mitigate ransomware and other threats to data security. It comprises:
- Monitoring, alerting, and emergency response,
- Accounting of authorized personnel activity,
- Disaster recovery,
- Reporting of criminal activity, and
- Forensic analysis.
Defense-in-depth security means recognizing that no one security solution is ever enough for healthcare organizations. The best cyber security experts find the right combination of new and tried-and-true techniques and tools that address the organization’s unique security and privacy requirements.
The diagram below depicts the guidelines suggested by the International Standards Organization’s ISO 27001 and ISO 27002 for Information Systems Management Security and Security Techniques, and principles such as the American Institute of CPA’s Generally Accepted Privacy Principles (GAPP) to determine security and privacy requirements.1
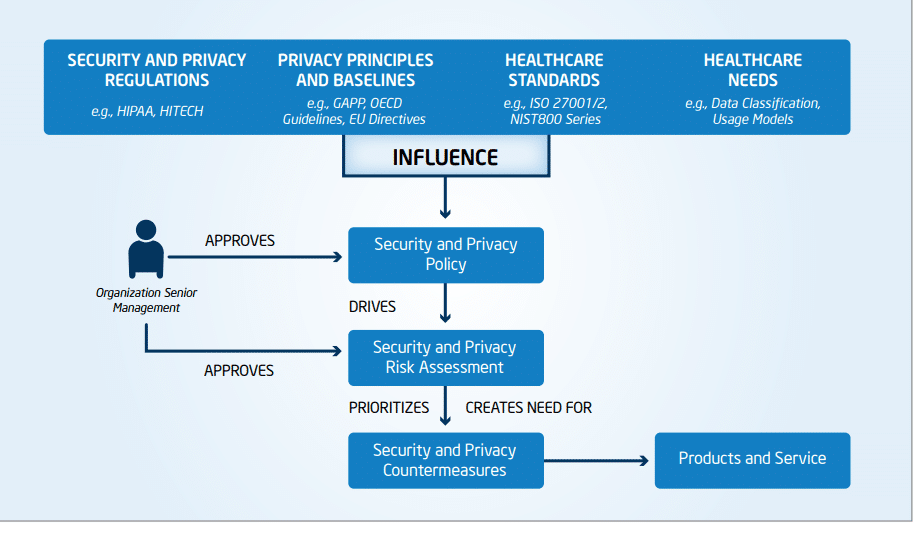
Only with a multi-layered, defense-in-depth strategy can healthcare organizations guard against patient safety infractions and best address the ever-increasing and evolving forms of ransomware.
Hopefully, this won’t happen, but if your hospital or healthcare facility is ever victimized by ransomware, be sure to contact the HHS for guidance.
For more information about Ransomware and Defense-in-Depth protection for your organization, contact Alvarez Technology Group at [email protected] or (831) 753-7677.
1. Intel: “Health Information at Risk: Successful Strategies for Healthcare Security and Privacy”





